Unveiling Security Risks in 6G: Exploring Vulnerabilities in Future Wireless Networks
Published in Electrical & Electronic Engineering
As the global deployment of 5G wireless communication technology continues, researchers and industry experts are already looking ahead to the future of 6G. This upcoming technology holds the potential to revolutionize wireless communications, offering unprecedented speeds, ultra-low latency, and vast connectivity. With promises of supporting advanced applications such as autonomous vehicles, augmented reality, and the Internet of Things, 6G is expected to usher in a new era of connectivity. However, as with any technological advancement, it is crucial to consider security and privacy as foundational principles in the design and implementation, to avoid repeating the vulnerabilities and shortcomings observed in previous generations.
Our study sheds light on the emerging risks associated with advanced electromagnetic wave manipulation techniques at the physical layer. As wireless communication systems evolve, programmable coding metasurfaces are gaining traction as a key enabling technology for 6G's smart radio channels. These metasurfaces, composed of subwavelength-sized elements that optimize wireless channels in scattering-rich environments, bring great potential but also introduce new avenues for attacks and vulnerabilities.
Striking a balance between leveraging metasurface capabilities to enhance communication efficiency and mitigating associated risks becomes a critical challenge. Our research uncovers that programmable metasurfaces, easily concealed in everyday objects like wallpapers or window glasses, have the power to alter information exchanged between multiple users and enable undetectable attacks on wireless signals. Such vulnerabilities raise significant concerns for the security and integrity of 6G networks.
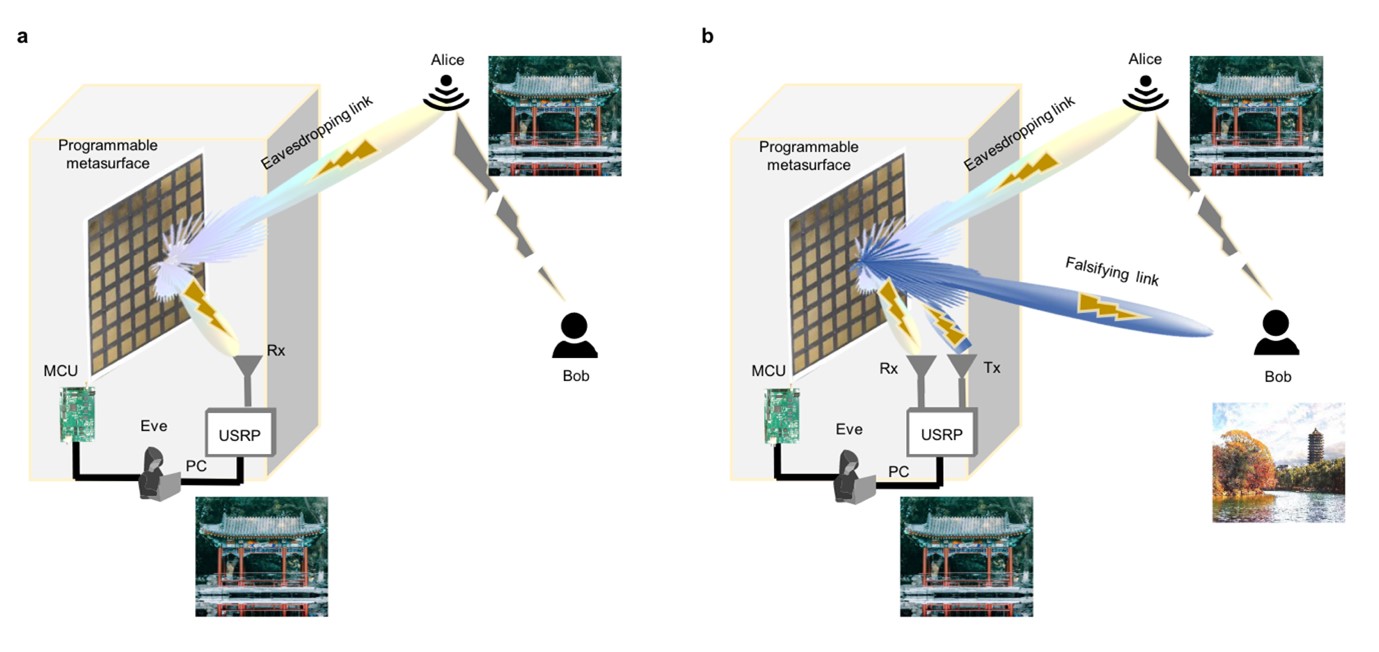
Figure 1: Schematics of metasurface-based wireless attacks. (a) Passive mode: Alice aims to wirelessly transmit information to Bob while Eve, an eavesdropper, exploits a programmable metasurface to intercept or disrupt the communication. (b) Active mode: Eve not only eavesdrops but also utilizes the metasurface to transmit deceptive data, falsifying the information received by Bob.
Rx: receiver; Tx: transmitter; PC: personal computer; URSP: universal software radio peripheral, MCU: micro control-unit.
Through our experiments, we demonstrated the capabilities of metasurface-based attackers in passive and active modes. In the passive mode (Figure 1a), an attacker (Eve) exploits a programmable metasurface to eavesdrop on wireless signals transmitted between legitimate users (Alice and Bob), enhancing the eavesdropped signal's power without leaving significant traces. In the active mode (Figure 1b), the attacker not only eavesdrops but also falsifies information by establishing a falsifying link and transmitting deceptive data. These attacks demonstrate minimal detectability, making them highly challenging to identify.
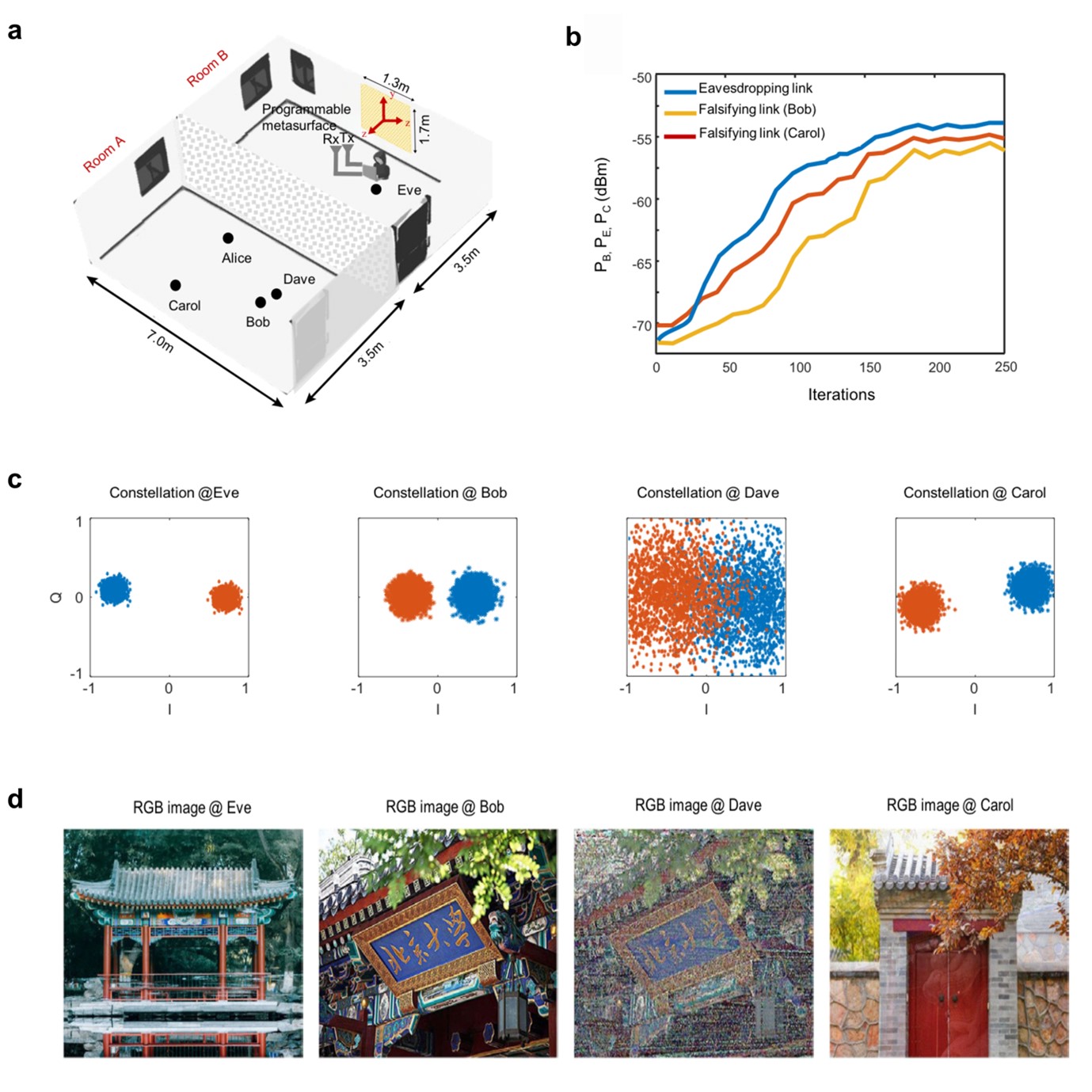 Figure 2: (a) Experimental setup for eavesdropping and falsification of information: Eve (in room B) intercepts and manipulates data intended for Bob and Carol from Alice (in room A); a nearby detector named Dave monitors the process. Also shown are the receivers (Rx) and a single-tone transmitter (Tx) at Eve's side. (b) Variation of eavesdropping and falsifying powers during metasurface coding-pattern optimization. (c) Decoded constellation diagrams of signals received by Eve, Bob, Dave, and Carol, illustrating the differences in signal quality. (d) RGB images acquired by Eve, Bob, Dave, and Carol, respectively, highlighting the attack's impact on the transmitted information.
Figure 2: (a) Experimental setup for eavesdropping and falsification of information: Eve (in room B) intercepts and manipulates data intended for Bob and Carol from Alice (in room A); a nearby detector named Dave monitors the process. Also shown are the receivers (Rx) and a single-tone transmitter (Tx) at Eve's side. (b) Variation of eavesdropping and falsifying powers during metasurface coding-pattern optimization. (c) Decoded constellation diagrams of signals received by Eve, Bob, Dave, and Carol, illustrating the differences in signal quality. (d) RGB images acquired by Eve, Bob, Dave, and Carol, respectively, highlighting the attack's impact on the transmitted information.
Figure 2a depicts the experimental setup where Eve, located in room B, aims to eavesdrop on and falsify information intended for Bob and Carol from Alice, located in room A. The goal is for Eve to remain undetectable to a potential detector named Dave. Using a programmable metasurface, Eve establishes independent falsifying links with Bob and Carol, transmitting deceptive data streams to them. For these latter, the metasurface utilizes a modulated backscattering wireless communication scheme, which was recently introduced by some of us [Nature Communications 11, 3926 2020, Nature Electronics 4, 218, 2021], allowing the encoding of deceptive data directly into the programmable metasurface. This enables the generation and manipulation of independent information-carrying radiation beams towards Bob, Carol, and Eve while minimizing Eve's detectability. An optimization process iteratively refines the metasurface coding pattern. Figure 2b shows the power levels of eavesdropping and falsifying at Eve's, Bob's, and Carol's sides during the optimization iterations. Figure 2c displays some typical constellation diagrams (for binary phase-shift keying modulation) of the received signals at Bob's, Eve's, Dave's, and Carol's sides, showing significantly degraded signal quality at Dave's side. Furthermore, assuming the transmission of an RGB image from Alice to Bob, Figure 2d illustrates Eve's ability to eavesdrop and falsify images received by Bob and Carol, while the image received by Dave is of notably lower quality. Further details and additional results can be found in the accompanying video:

On the basis of these results, we can conclude that the proposed metasurface-based wireless attacker is capable of eavesdropping, disrupting and/or falsifying simultaneously the data streams in complicated indoor environments, while maintaining a low detectability. While our study primarily focuses on 2.4GHz Wi-Fi signals, the implications of these attacks extend to a wide range of wireless communication systems.
In light of these findings, proactive measures need to be taken to address the potential vulnerabilities in 6G communications. Strategies such as beamforming can be explored to mitigate the impact of these attacks, along with other techniques like cooperative jamming with artificial noise, index modulation, and adaptive modulation. The design and implementation of secure 6G networks should consider both the advantages and challenges associated with programmable metasurfaces, and actively develop countermeasures to protect against potential attacks and ensure the confidentiality, integrity, and availability of wireless communications.
In conclusion, as we move towards the era of 6G communications, it is essential to be mindful of potential vulnerabilities and risks. Our research highlights the importance of understanding the implications of advanced electromagnetic wave manipulation techniques and programmable coding metasurfaces on the security of wireless communications. Continuing our work, we are actively investigating countermeasures specifically tailored to mitigate the risks posed by programmable metasurface attacks in the context of 6G communications.
For more details see[Nature Electronics, 2023].
Follow the Topic
-
Nature Electronics

This journal publishes both fundamental and applied research across all areas of electronics, from the study of novel phenomena and devices, to the design, construction and wider application of electronic circuits.




Please sign in or register for FREE
If you are a registered user on Research Communities by Springer Nature, please sign in