Breaking universal limitations on quantum conference key agreement without quantum memory
Published in Physics
The conference key agreement is a cryptographic primitive that shares information-theoretic secure keys among more than two authenticated users for group encryption and decryption. Classical conference key agreement is no longer secure in the face of an eavesdropper with quantum resources. Multiple quantum key distribution links can be applied to protect against quantum eavesdroppers, which is suboptimal in communication efficiency. Alternatively, multipartite entangled states can be used to realize conference key agreement for achieving a genuine advantage over point-to-point quantum communication protocols [1].
In this work, we propose an adaptive quantum conference key agreement (QCKA) protocol using post-selected multipartite entangled states and spatial multiplexing. Our QCKA protocol distributes conference keys with post-selected Greenberger-Horne-Zeilinger (GHZ) states—an entangled state introduced to reveal the extreme violation of local realism against quantum mechanics. The GHZ entanglement can be transmitted directly through the quantum channel to communication parties in the network, and then each party can establish conference keys by measuring the received state. Directly distributing GHZ entanglement is quite unpractical for large-scale deployment due to the low key rate caused by the channel loss and the fragility of the GHZ entanglement resources. To avoid requiring entanglement preparation beforehand, a scheme for distributing the post-selected GHZ entanglement was proposed [2]. In this scheme, each party in the network sends a randomly selected single-photon state to an untrusted central node. The central node performs GHZ projection on the incoming single-photon states, and the trials where the incoming states are successfully projected on the GHZ state can be utilized to establish conference keys with classical postprocessing. This scheme is immune to all detection-side attacks and thus it is called measurement-device-independent (MDI) QCKA. However, the key rate of this original MDI QCKA protocol is limited when the number of users increases.
Inspired by the all-photonic quantum repeater [3] and MDI adaptive quantum key distribution [4], our protocol uses the idea of spatial multiplexing and adaptive operation to overcome the key rate limitations on quantum communication over a network. To be specific, in all-photonic quantum repeater, each user prepares and sends multiple single photons maximally entangled with local qubits to an adjacent receiver node. At the same time, any other source node prepares the encoded complete-like cluster state and sends the left arms (right arms) to the left-hand (right-hand) adjacent receiver node. The receiver node applies Bell state measurement to the second leaf of the received qubits. Since the Bell state measurement succeeds probabilistically, the receiver node performs X- or Z-basis measurement adaptively and the bipartite entanglement can be established. This idea is also applied in adaptive MDI quantum key distribution protocol, where both users send multiple single photon states simultaneously to the central node who subsequently confirms the arrival of photons by applying quantum non-demolition (QND) measurement and pairs the arrived photons adaptively. Our protocol follows a similar way as shown in Figure 1. In Figure 1 (a) we show the network structure of our protocol with n user nodes. The detailed process between node Ai and the central node C is depicted in Figure 1 (b).
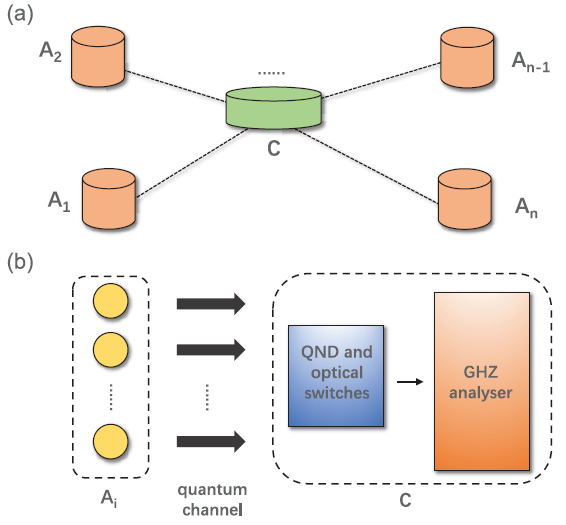
Figure 1: Schematic of our protocol. (a) Network structure of our protocol with n user nodes. (b) Detailed process between Ai and the node C. Ai prepares and transmits multiple quantum signals to the central node C through quantum channel. At node C the signals are confirmed by QND measurement and then routed to the GHZ analyser through optical switches. In this process, spatial multiplexing and adaptive operations are used to improve the efficiency of our protocol.
To investigate the performance of our protocol, we first analyse and prove that the efficiency of the successful GHZ projection remains proportional to the total loss regardless of the number of communication parties, which is a significant enhancement compared with the original MDI QCKA [2]. We also perform numerical simulations to calculate the key rate of our protocol at different distances within the experimentally feasible parameter regime. To show the performance, our work considers a rate benchmark called the direct transmission bound where one user is selected and performs quantum key distribution with every one of the rest n − 1 users to establish bipartite secret keys with the same length due to the network symmetry. The selected user can encode the conference key with the established keys to conduct the conference key agreement. In Figure 2, we plot the key rates of our QCKA as well as the direct transmission bound as a function of distance with different numbers of communication parties. From the simulation results, regardless of the increasing number of communication parties, a polynomial scaling of efficiency with distance can be realized while the bounds attenuate greatly. We also compare the key rate of our protocol with other QCKA and establish the security analysis in the finite-key regime.
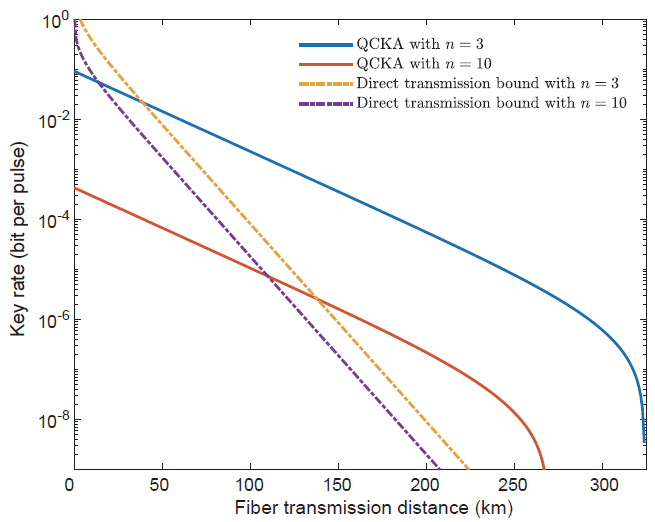
In conclusion, we report an MDI QCKA protocol for the quantum network application. We analyse the security of the QCKA protocol and provide a computable key length in the finite-size regime. Compared with the direct transmission bound of quantum communication over quantum network, our protocol shows great superiority in deploying in large-scale quantum network. Based on the results of this work, we can anticipate a wide usage of our work in multiparty applications of secure quantum network.
References
[1] M. Epping, H. Kampermann, C. Macchiavello, and D. Bruß, Multi-partite entanglement can speed up quantum key distribution in networks, New J. Phys. 19, 093012 (2017).
[2] Y. Fu, H.-L. Yin, T.-Y. Chen, and Z.-B. Chen, Long-Distance Measurement-Device-Independent Multiparty Quantum Communication, Phys. Rev. Lett. 114, 090501 (2015).
[3] K. Azuma, K. Tamaki, and H.-K. Lo, All-photonic quantum repeaters, Nat. Commun. 6, 6787 (2015).
[4] K. Azuma, K. Tamaki, and W. J. Munro, All-photonic intercity quantum key distribution, Nat. Commun. 6, 10171 (2015).
Follow the Topic
-
Communications Physics

An open access journal from Nature Portfolio publishing high-quality research, reviews and commentary in all areas of the physical sciences.
Related Collections
With Collections, you can get published faster and increase your visibility.
Higher-order interaction networks 2024
Publishing Model: Open Access
Deadline: Feb 28, 2026
Physics-Informed Machine Learning
Publishing Model: Hybrid
Deadline: May 31, 2026

Please sign in or register for FREE
If you are a registered user on Research Communities by Springer Nature, please sign in